Resources
About Us
Zero Trust Security Market by Component (Solutions, Services), Deployment Model (Cloud, On-Premises, Hybrid), Organization Size, Authentication Method, and Industry Vertical – Global Forecast to 2036
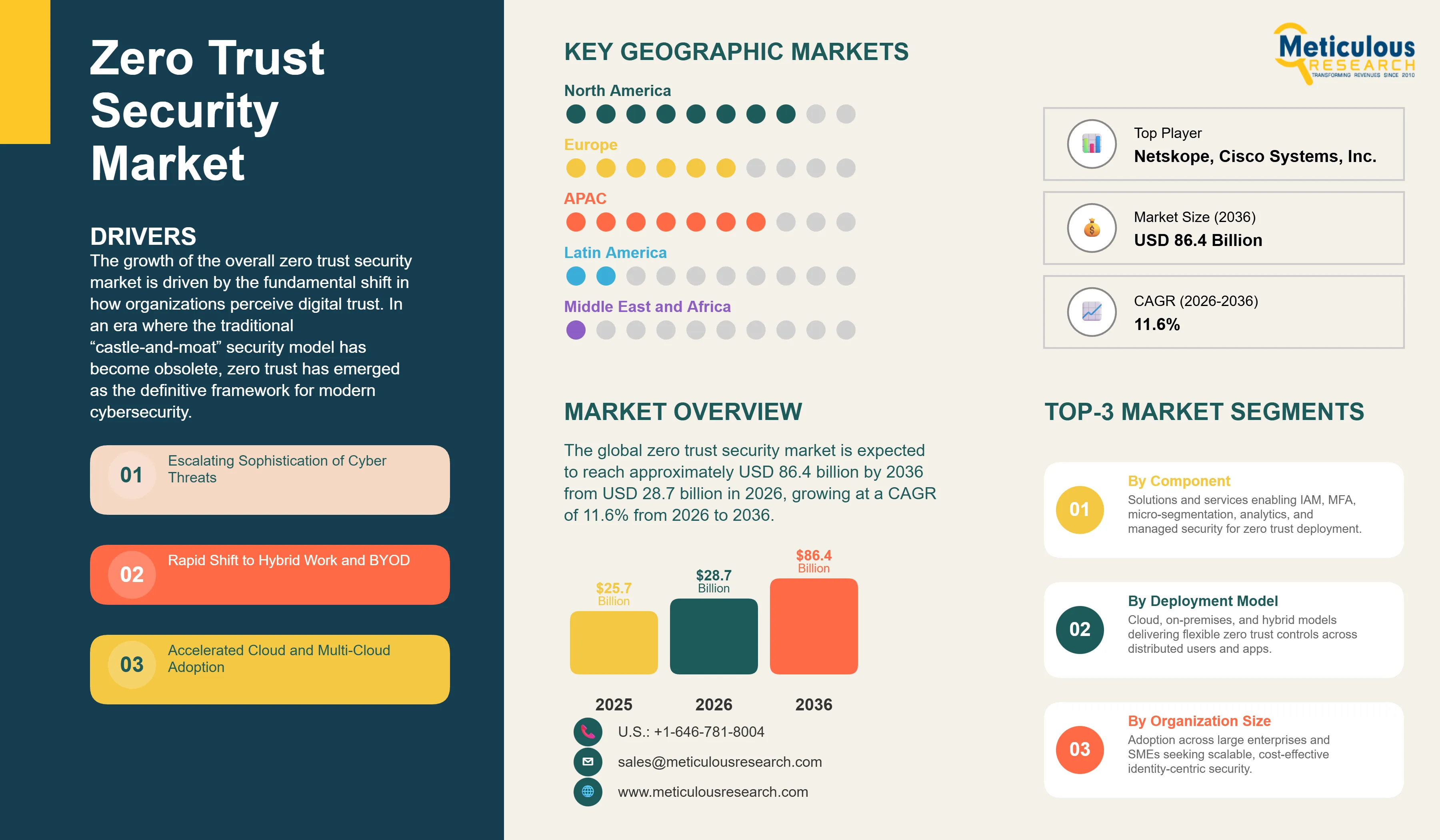
Report ID: MRICT - 1041704 Pages: 267 Feb-2026 Formats*: PDF Category: Information and Communications Technology Delivery: 24 to 72 Hours Download Free Sample ReportThe global zero trust security market was valued at USD 25.7 billion in 2025. The market is expected to reach approximately USD 86.4 billion by 2036 from USD 28.7 billion in 2026, growing at a CAGR of 11.6% from 2026 to 2036.
The growth of the overall zero trust security market is driven by the fundamental shift in how organizations perceive digital trust. In an era where the traditional “castle-and-moat” security model has become obsolete, zero trust has emerged as the definitive framework for modern cybersecurity. By operating on the core principle of “never trust, always verify,” this architecture ensures that every access request—whether it originates from inside or outside the network—is continuously authenticated and authorized. The rapid expansion of the hybrid workforce, the proliferation of cloud-native applications, and the increasing sophistication of ransomware attacks have made zero trust a business necessity rather than a technical luxury. As enterprises look to build resilient digital ecosystems, the adoption of zero trust principles continues to fuel significant growth across all major geographic regions.
 Click here to: Get Free Sample Pages of this Report
Click here to: Get Free Sample Pages of this Report
Zero trust security represents a profound shift in the cybersecurity mindset—moving away from protecting a fixed perimeter to protecting individual data flows and identities. In today’s world, where employees work from anywhere and applications live in the cloud, the “perimeter” has effectively disappeared. Zero trust addresses this reality by assuming that threats are already present within the network. It treats every user, device, and application as a potential risk, requiring explicit verification through multiple layers of security—such as identity checks, device health assessments, and behavioral analytics—before granting the minimum necessary access. This “least-privilege” approach ensures that even if an attacker gains entry, their ability to move laterally and cause widespread damage is severely restricted.
The market is defined by a convergence of advanced technologies, including Identity and Access Management (IAM), Multi-Factor Authentication (MFA), and network micro-segmentation. These tools work together to create a dynamic security environment that adapts to the risk level of each access request. For instance, a user logging in from a known corporate laptop might have a different access profile than the same user connecting from a personal mobile device in a public space. This contextual awareness is what makes zero trust so effective against modern threats like credential theft and social engineering. By focusing on the “who, what, where, and when” of every interaction, organizations can build a security posture that is both robust and flexible.
The global push for digital modernization is a major catalyst for zero trust adoption. As businesses migrate to multi-cloud environments and integrate millions of IoT devices, the attack surface expands exponentially. Zero trust provides a consistent security framework that spans these diverse environments, ensuring that data remains protected regardless of where it resides. Furthermore, the rise of “Security-as-a-Service” (SECaaS) has made zero trust more accessible, allowing organizations to leverage cloud-native security tools that are easier to deploy and manage than traditional on-premises appliances.
In a zero trust world, identity has become the primary security boundary. Modern implementations recognize that verifying “who” is requesting access is more important than “where” they are connecting from. This trend is driving the adoption of sophisticated IAM platforms that offer adaptive authentication—adjusting security requirements in real-time based on the user’s behavior and risk context. By integrating AI and machine learning, these platforms can detect anomalies, such as a login attempt from an unusual location or at an odd hour, and automatically trigger additional verification steps. This identity-centric approach allows businesses to provide a seamless user experience while maintaining a high level of security across all digital touchpoints.
The market is witnessing a significant convergence of networking and security through the Secure Access Service Edge (SASE) model. SASE combines zero trust principles with cloud-delivered networking, providing secure access to applications and data from the “edge” of the network—closer to where the users actually are. This eliminates the latency and bottlenecks associated with traditional VPNs, which were never designed for the scale of today’s remote workforces. By delivering security as a cloud service, SASE allows organizations to enforce consistent policies globally, ensuring that every connection is inspected and verified, whether the user is in a corporate office or a home office.
|
Parameter |
Details |
|
Market Size by 2036 |
USD 86.4 Billion |
|
Market Size in 2026 |
USD 28.7 Billion |
|
Market Size in 2025 |
USD 25.7 Billion |
|
Market Growth Rate (2026-2036) |
CAGR of 11.6% |
|
Dominating Region |
North America |
|
Fastest Growing Region |
Asia-Pacific |
|
Base Year |
2025 |
|
Forecast Period |
2026 to 2036 |
|
Segments Covered |
Component, Deployment, Org Size, Authentication, Vertical, and Region |
|
Regions Covered |
North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa |
The primary driver for zero trust adoption is the sheer scale and complexity of modern cyberattacks. High-profile ransomware incidents have shown that even the most well-defended perimeters can be breached. Attackers are increasingly using legitimate credentials and exploiting trust relationships to move undetected within networks for months. Zero trust directly addresses this by assuming a “breach mindset”—it assumes the attacker is already inside and uses continuous monitoring and micro-segmentation to limit their impact. For many organizations, the cost of a single data breach far outweighs the investment required to implement a zero trust framework, making it a clear strategic priority.
The transition to zero trust presents a unique opportunity for organizations to modernize their aging IT infrastructure. Implementing zero trust often involves auditing existing assets, cleaning up over-privileged accounts, and moving away from clunky legacy VPNs. This process not only improves security but also enhances operational efficiency and user productivity. Furthermore, as governments around the world mandate zero trust for their own agencies, a massive market is opening up for vendors who can provide compliant, high-performance security solutions. The “zero trust journey” is becoming a roadmap for broader digital transformation.
The solutions segment, which includes the hardware and software required to build a zero trust environment, accounts for the majority of the market share in 2026. This is because the initial phase of zero trust adoption typically involves significant capital investment in foundational technologies like IAM, MFA, and endpoint security. Organizations are prioritizing the “tools of the trade” to establish a baseline of continuous verification. As these technologies become more integrated and automated, the focus is shifting toward comprehensive platforms that can manage security policies across the entire enterprise.
However, the services segment is expected to grow at a rapid pace. Implementing zero trust is a complex, multi-year journey that requires expert guidance. From initial consulting and architecture design to ongoing managed security services, organizations are increasingly relying on third-party experts to help them navigate the technical and cultural challenges of the transition.
The cloud deployment model is witnessing the highest growth rate as organizations move away from managing physical security appliances. Cloud-delivered zero trust solutions offer several advantages, including faster deployment, automatic updates, and the ability to scale security as the business grows. This is particularly important for supporting a hybrid workforce, where security needs to be as mobile as the employees. By leveraging the global infrastructure of cloud providers, businesses can ensure that their security policies are enforced consistently, regardless of where their data or users are located.
On-premises and hybrid models remain relevant for organizations with strict data residency requirements or significant investments in legacy data centers. However, even these organizations are increasingly adopting “cloud-managed” security, where the control plane lives in the cloud while the enforcement points remain local.
North America continues to lead the global zero trust market, largely due to a combination of early adoption and strong regulatory pressure. The U.S. federal government’s mandate for agencies to adopt zero trust has set a high bar for the private sector, encouraging businesses of all sizes to follow suit. Additionally, the region is home to many of the world’s leading cybersecurity vendors, fostering a highly competitive and innovative market. The high concentration of data-intensive industries, such as finance and healthcare, further drives the demand for advanced security frameworks.
Asia-Pacific is the fastest-growing region, driven by a massive wave of digital transformation and cloud migration. As countries like China, India, and Singapore build out their digital economies, they are leapfrogging traditional security models in favor of zero trust. In Europe, growth is supported by stringent data privacy laws like GDPR, which require organizations to implement robust access controls and data protection measures. The European market is also seeing increased collaboration between governments to build sovereign, secure digital infrastructures.
The market is led by established technology giants and specialized cybersecurity firms, including Microsoft Corporation, Cisco Systems, Inc., Palo Alto Networks, Inc., Zscaler, Inc., and CrowdStrike Holdings, Inc. These companies offer comprehensive zero trust platforms that integrate identity, network, and endpoint security. Other key players like Okta, Inc., Fortinet, Inc., Check Point Software Technologies, and Akamai Technologies provide specialized solutions for identity management, secure access, and cloud protection. Emerging innovators such as Illumio, Netskope, and SentinelOne are also gaining significant traction by focusing on niche areas like micro-segmentation and AI-driven threat detection.
The zero trust security market is expected to grow from USD 28.7 billion in 2026 to USD 86.4 billion by 2036.
The zero trust security market is expected to grow at a CAGR of 11.6% from 2026 to 2036.
Major players include Microsoft, Cisco, Palo Alto Networks, Zscaler, CrowdStrike, Okta, Fortinet, Check Point, Akamai, Cloudflare, VMware, IBM, AWS, Google, and Netskope, among others.
Main factors include escalating cyberattacks and ransomware requiring advanced security, hybrid workforce transformation necessitating secure remote access, cloud migration creating distributed IT environments, regulatory mandates (Executive Order 14028, GDPR), and digital transformation expanding attack surfaces.
North America is estimated to account for the largest share in 2026 due to advanced cybersecurity infrastructure and regulatory mandates, while Asia-Pacific is expected to register the highest growth rate during 2026-2036 driven by digital transformation and cloud adoption.
























Published Date: Jul-2024
Published Date: Apr-2024
Published Date: Jan-2024
Published Date: Aug-2022
Published Date: Jul-2022
Please enter your corporate email id here to view sample report.
Subscribe to get the latest industry updates